IEC 104 redundancy server modes
Multiple redundancy groups
The MZ Automation lib60870 server provides 3 different modes regarding the support of redundant connections and events queue handling:
- The default mode (CS104_MODE_SINGLE_REDUNDANCY_GROUP) allows only a single active client connection.
- The second mode (CS104_MODE_CONNECTION_IS_REDUNDANCY_GROUP) allows multiple active client connections.
- The third mode (CS104_MODE_MULTIPLE_REDUNDANCY_GROUPS) allows multiple active client connections while preserving events when no client is connected.
In the case of this design, the south plugin will be implemented with CS104_MODE_MULTIPLE_REDUNDANCY_GROUPS server mode.
This mode allows multiple active client connections while preserving events when no client is connected. In this mode clients can be assigned to specific redundancy groups. The assignment is based on the IP address of the client. A redundancy group can have multiple simultaneous connections but only one of these connections can be active. The number of activated connections is restricted by the number of redundancy groups. Each redundancy group has a dedicated event queue.
It can be set with the CS104_Slave_setServerMode function:
CS104_Slave_setServerMode(slave, CS104_MODE_MULTIPLE_REDUNDANCY_GROUPS);
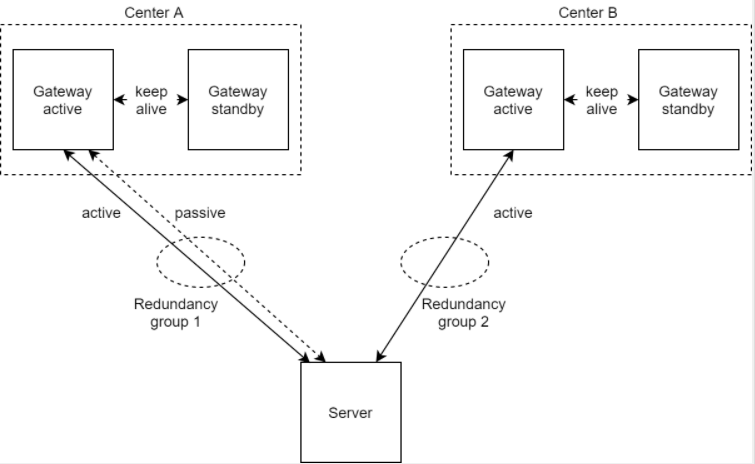
Multiple redundancy groups example
In this example, 2 control centers, center A and B, are establishing communication with the server.
Both centers have an active and a stand-by gateway for failover management.
Center A has two simultaneous connections, one active and one stand-by, assigned to redundancy group 1.
Center B has only one active connection, assigned to redundancy group 2.
IEC 104 Protocol stack configuration
The IEC 104 protocol stack configuration specifies communication parameters and is a collection of entries containing information about OSI Transport and OSI Application layers objects.
Each entry is comprised of attributes that describe the object. All the configuration data are structured using JSON.
Each entry shall be mapped with the corresponding configuration function in the chosen implementation protocol library.
Attributes definition
| Attribute | Description | Expected values | Mandatory |
|---|---|---|---|
| name | this identifies the protocol stack | iec104client, iec104server, tase2client, tase2server, 61850client, 61850server, etc... | Yes |
| version | version number of the configuration file | 2 digits x.y => x = major change, y = minor change | Yes |
| redundancy_groups | array of redundancy groups | Yes | |
| redundancy_groups.connections | array of connections of a given redundancy group | Yes | |
| redundancy_groups.connections.clt_ip | IEC 104 client address | IP address | Yes |
| redundancy_groups.rg_name | this identifies the redundancy group | Any non empty string | Yes |
| srv_ip | Server IP address | IP address, machine's default IP for a given interface, default = 0.0.0.0 | No |
| port | This defines the TCP/IP port to be used by the server. | default = 2404 | No |
| tls | activation of TLS (see tls configuration chapter for details) | TRUE, FALSE, default = FALSE | No |
| k_value | Maximum number of outstanding (unacknowledged) APDU's at a given time | default = 12, range : 1 to 32767 | No |
| w_value | Acknowledge the reception latest after this number of APDU's | default = 8, range : 1 to 32767 | No |
| t0_timeout | time out of connection establishment | default = 30 seconds, range : 1 to 255 | No |
| t1_timeout | time out for send or test APDU's | default = 15 seconds, range : 1 to 255 | No |
| t2_timeout | time out for acknowledges in case of no data messages (t2 < t1) | default = 10 seconds, range : 1 to 255 | No |
| t3_timeout | time out for sending test frames | default = 20 seconds, range : 1 to 172800 | No |
| mode | "accept_always": accept connection or maintain connection with center independently from the south asset connection status "accept_if_south_connx_started": accept connection or maintain connection with center only if south asset connection is established and running | default = "accept_always", enum: "accept_always" or "accept_if_south_connx_started" | |
| ca_asdu_size | size of "Common Address of ASDU" | default = 2 (byte), enum: 1 or 2 | No |
| ioaddr_size | size of 'Information Object Address' | default = 3 (byte), enum: 1, 2 or 3 | No |
| asdu_size | maximum ASDU size in transmission direction, if set to "0" => maximum possible value is automatically used. | default = 0 (byte), range : 0 to 255 | No |
| asdu_queue_size | minimum number of ASDUs that can be stored in the asdu buffer | default = 100 | No |
| time_sync | If set on "TRUE" this parameter allows to synchronize the clock of the local computer by the server. If set on "FALSE", the clock is not synchronized. | TRUE, FALSE, default = FALSE | No |
| cmd_exec_timeout | Defines the command execution monitoring timeout in seconds. | default = 20 seconds, range : 1 to 3 600 | No |
| cmd_recv_timeout | This parameter defines the highest allowable deviation of received command time tag and local clock in seconds. If the difference is too big, command is ignored. | default = 0 (disabled), range : 0 to 3 600 | No |
| accept_cmd_with_time | If set to 0, then accept no commands with timestamp, if set to 1 accept only commands with timestamp, if set to 2, then accept both | default =1, enum: 0, 1 or 2 | No |
| filter_list | List of Authorized Originators (array) → only commands from authorized originator addresses are accepted. | default = empty | No |
| filter_list.orig_addr | Originator address | enum: 0, 1, ..., N | |
| cmd_dest | Defines the destination service on which to execute the command | default = broadcast | No |
| south_monitoring | connection loss and gi failure handling feature | Yes | |
| south_monitoring.assets | array of assets name used to monitor the connection and gi status information from the south | default = [CONSTAT-1, CONSTAT-2] | No |
Configuration JSON structure
{
"protocol_stack":{
"name":"iec104server",
"version":"1.0",
"transport_layer":{
"redundancy_groups":[
{
"connections":[
{
"clt_ip":"192.168.0.10"
},
{
"clt_ip":"192.168.0.11"
},
{
"clt_ip":"10.152.1.10"
},
{
"clt_ip":"10.152.1.11"
}
],
"rg_name":"red-group-1"
},
{
"connections":[
{
"clt_ip":"192.168.0.10"
},
{
"clt_ip":"192.168.0.11"
},
{
"clt_ip":"192.168.0.12"
},
{
"clt_ip":"192.168.0.14"
},
{
"clt_ip":"10.152.1.10"
},
{
"clt_ip":"10.152.1.11"
},
{
"clt_ip":"10.152.1.12"
},
{
"clt_ip":"10.152.1.13"
}
],
"rg_name":"red-group-2"
},
{
"rg_name":"catch-all"
}
],
"srv_ip":"0.0.0.0",
"port":2404,
"tls":false,
"k_value":12,
"w_value":8,
"t0_timeout":30,
"t1_timeout":15,
"t2_timeout":10,
"t3_timeout":20,
"mode":"accept_always"
},
"application_layer":{
"ca_asdu_size":2,
"ioaddr_size":3,
"asdu_size":0,
"asdu_queue_size":100,
"time_sync":false,
"cmd_exec_timeout":20,
"cmd_recv_timeout":0,
"cmd_dest":"broadcast",
"accept_cmd_with_time":1,
"filter_list":[
{
"orig_addr":1
},
{
"orig_addr":2
}
]
},
"south_monitoring":[
{
"asset":"CONSTAT-1"
},
{
"asset":"CONSTAT-2"
}
]
}
}
TLS configuration
The CS 104 standard can also be used with TLS to realize secure and authenticated connections.
Parameters are needed to set up the TLS secured connection:
| Attribute | Description | Expected values | Mandatory |
|---|---|---|---|
| private_key | server private key | valid private key | YES |
| own_cert | server certificate | valid certificate | YES |
| ca_certs | allows to specify the ca certificates if not included in the owner certificate | list of valid certificates | NO |
| remote_certs | allows to specify the clients certificates, so if specified, only these certificates are accepted | list of valid certificates | NO |
Fledge's certificate store allows certificates to be stored and used by the south plugins.
{
"private_key":"iec104_server.key",
"own_cert":"iec104_server.cer",
"ca_certs":[
{
"cert_file":"iec104_ca.cer"
},
{
"cert_file":"iec104_ca2.cer"
}
],
"remote_certs":[
{
"cert_file":"iec104_client.cer"
}
]
}
IEC 104 datapoint representation
This is the Datapoint representation of an IEC 104 ASDU for a command.
The current implementation does not use a json structure, so the order of parameters is mandatory.
| Order | Attribute JSON (not currently used) | Description | Expected values | Mandatory |
|---|---|---|---|---|
| 0 | co_type | Type of ASDU | YES | |
| 1 | co_ca | Common Address of ASDU | YES | |
| 2 | co_ioa | Information object address | YES | |
| 3 | co_cot | Cause of Transmission | YES | |
| 4 | co_negative | is negative command ? | 0 or 1 = negative | YES |
| 5 | co_se | Select or Execute | 0 = Direct execute or 1 = Select before Execute | YES |
| 6 | co_test | is test command ? | 0 or 1 = test | YES |
| 7 | co_ts | timestamp | YES | |
| 8 | co_value | Value | YES | |
| 9 | co_qu | is pulse defined ? | 0 or 1 = pulse defined | NO |
Below is an example of an instance of an Operation object :
operation: {
type: "IEC104Command",
nbParams=9,
names=[
"co_type",
"co_ca",
"co_ioa",
"co_cot",
"co_negative",
"co_se",
"co_test",
"co_ts",
"co_value"
],
parameters=[
"C_SC_TA_1",
"21441",
"74",
"7",
"0",
"0",
"0",
"1701426945586",
"1"
],
cmdDest="hnzsouth_s1"
}